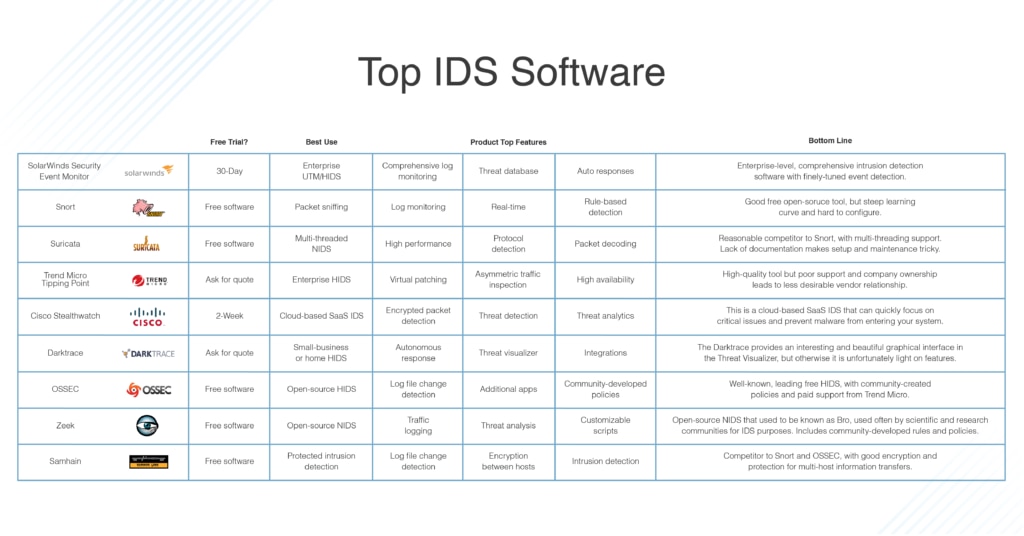
An Ids May Use Which of the Following Techniques
Misuse method allows detecting know attacks which means new attacks cannot be detected whereas anomaly based detection method allows detecting new attacks when observing deviation from normal. It then identifies and alerts the admins to unusual behavior across network bandwidth devices ports protocols etc.
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff
Which of the following IDS detection technique detects the intrusion based on the fixed behavioral characteristics of the users and components in a computer system.

. Fragmentation obfuscation and encryption are all evasive techniques used by attackers to dodge IDS detection. A HIDS tracks only incoming and outgoing network packets and alerts the administrator to unusual or malicious behavior. These techniques could include fragmentation low-bandwidth attacks pattern change evasion address spoofing or proxying and more.
Signature recognition Anomaly detection Protocol anomaly detection All of the above. Contents 1 Obfuscation 11 Encoding 12 Polymorphism 2 Evasion 21 Fragmentation and small packets 22 Overlapping fragments and TCP segments 23 Ambiguities 24 Low-bandwidth attacks. Such an IDS may have the ability to monitor network traffic to and.
________ maps displays colors shades or patterns in accordance with category values of underlying data. A arrange for the purchase and sale of goods. And like many cybersecurity solutions an IDS can either be host-based or network-based.
A network intrusion detection system NIDS is crucial for network security because it enables you to detect and respond to malicious traffic. A host-based IDS is deployed on a particular endpoint and designed to protect it against internal and external threats. Following are some of the techniques used to evade and bypass an IDS.
Host intrusion detection system HIDS. An IDS can be used to help analyze the quantity and types of attacks. Intrusion detection systems are designed to be deployed in different environments.
By sending fragmented packets the attacker will be under the radar and can easily bypass the detection systems ability to detect the attack signature. An intrusion detection system can also help companies identify bugs. Insertion attack -In an insertion attack the attacker tries to confuse the IDS by sending invalid packets.
False positives ie generating alerts when. Use modules or IOS software-based IPSIDS if you can not afford appliances. A arrange for the purchase and sale of goods.
An IDS that shuts down the Internet after a. Functions of the Intrusion Detection system in the network security Following are the functions of IDS which make it popular among its various clients It keeps an eye on the functions of routers firewalls key management servers and files. IDS may be used either as a software application or as a network security appliance.
The attacker crafts a malformed packet in such a way that the end system interprets the attack payload correctly but the IDS is unable to recognize the attack. This IDS approach monitors and detects malicious and suspicious traffic coming to and going from all devices connected to the network. Use automated signature updates when possible 6.
D sell services that they provide. Question 4 of 15 70 Points Which of. Denial-of-service and access attacks are forms of attacks performed by hackers but are not directly used to compromise IDSs.
C take title to the goods they sell. Network intrusion detection system NIDS. A comprehensive intrusion detection system IDS can understand the evasion techniques cybercriminals use to trick an intrusion prevention system into thinking there isnt an attack taking place.
Most IDSs have been modified to detect or even reverse basic evasion techniques but IDS evasion and countering IDS evasion are still active fields. ISSC362 Week 8 Quiz Question 1 of 15 70 Points Which of the following properly describes an IDS system. A NIDS solution is deployed at strategic points within an organizations network to monitor incoming and outgoing traffic.
The primary benefit of an intrusion detection system is to ensure IT personnel is notified when an attack or network intrusion might be taking place. Primarily an IDS is concerned with the detection of hostile actions. Warnings may be irrelevant.
In this ultimate guide Ill go through everything you. There are several different types of IDS and numerous tools on the market and figuring out which one to use can be daunting. This network security tool uses either of two main techniques described in more detail below.
Intrusion detection systems do have several recognized management challenges that may be more work than an organization is willing or able to take on. B include B2C B2B and B2G transactions. It also detects on the basis of the already known malicious instruction sequence that is used by the malware.
Signature-based IDS detects the attacks on the basis of the specific patterns such as number of bytes or number of 1s or number of 0s in the network traffic. What does active detection refer to when using an intrusion detection system IDS. The first one anomaly detection explores issues in intrusion detection associated with deviations from normal system or user behavior.
A HIDS system is installed on individual. Take advantage of global correlation to improve resistance against attacks that may be moving towards your organization. Organizations can use this information to change their security systems or implement more effective controls.
A network intrusion detection system NIDS monitors. There are a number of techniques which attackers are using the following are considered simple measures which can be taken to evade IDS. Use a risk-based approach where countermeasures occur based on the calculated risk rating.
Select all that apply An IDS that is constantly running 24 hours a day. Anomaly-Based Intrusion Detection System AIDS This type of IDS is based on a method or an approach where the program monitors your ongoing network traffic and analyzes its pattern against predefined norms or baseline. Answers B D and E are correct.
An IDS that responds to the suspicious activity by logging off a user An IDS that reprograms the firewall to block the suspected source. HIDS Host Intrusion Detection System NIDS Network Intrusion Detection System HIDS Host Intrusion Detection System Host intrusion detection HIDS systems run on different hosts or network devices. Detection Method of IDS.
An intrusion detection system IDS is a tool or software that works with your network to keep it secure and flag when somebody is trying to break into your system.

8 Highly Effective Email List Building Techniques Email List Building List Building Email List
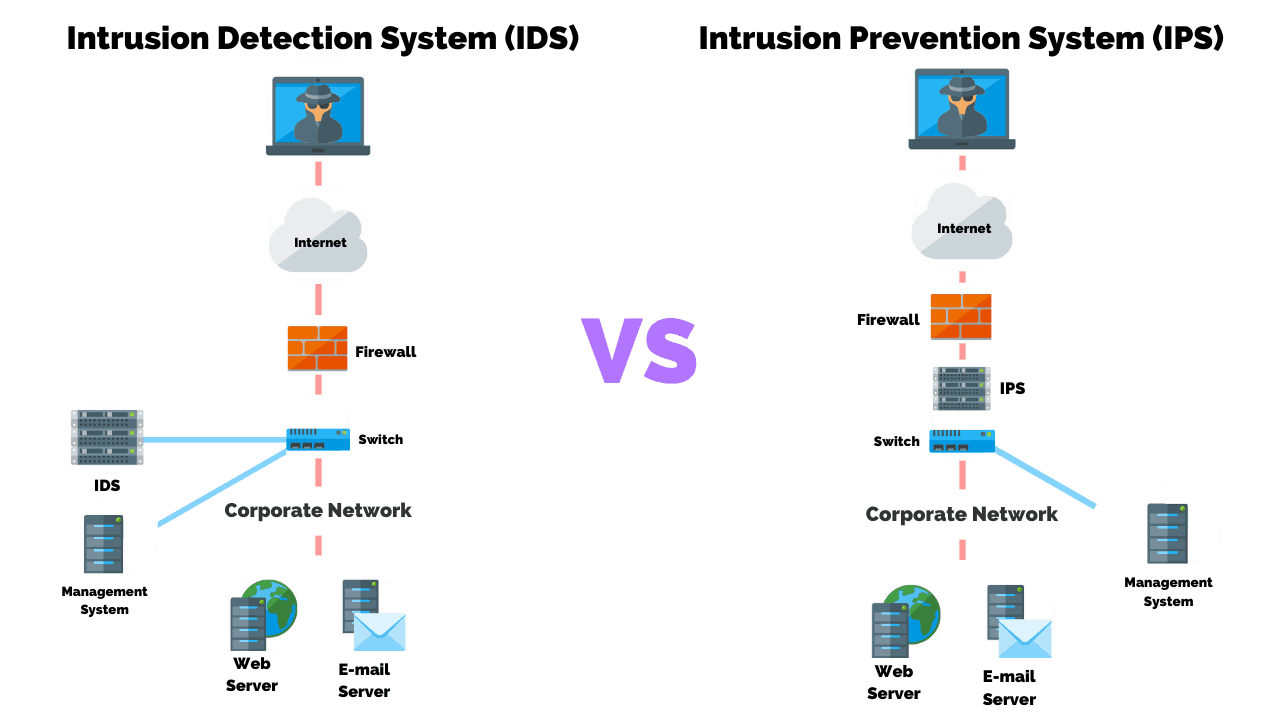
Intrusion Detection Vs Prevention Systems What S The Difference
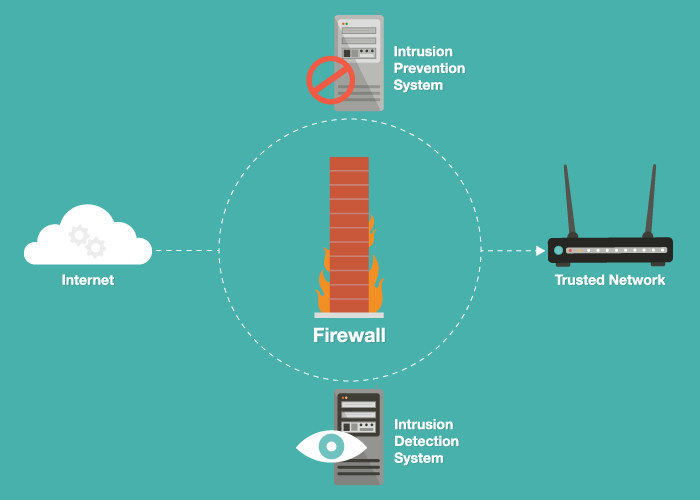
What Type Of Intrusion Detection And Prevention System Do I Need
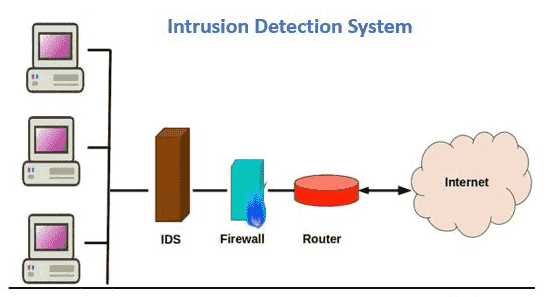
No comments for "An Ids May Use Which of the Following Techniques"
Post a Comment